For small and medium-sized businesses (SMBs), cybersecurity has become a critical concern. Yet most SMBs lack the resources, expertise, and budget to build comprehensive in-house security programs. This is where Managed Security Service Providers (MSSPs) become invaluable partners.
At ThreatRepel, we’ve seen firsthand how the right security partnership transforms businesses from vulnerable targets into cyber-resilient organizations. Let’s explore why working with an MSSP makes sense for your business.
What is a Managed Security Service Provider?
A Managed Security Service Provider (MSSP) is an external cybersecurity partner that provides ongoing security services to protect your business from cyber threats. Rather than building and maintaining your own security team and infrastructure, you outsource this critical function to specialists who do it every day for multiple clients.
MSSPs handle everything from monitoring your systems for threats to responding to security incidents, allowing your business to focus on what it does best while experts manage your cybersecurity.
Core Services MSSPs Provide
24/7 Security Monitoring
MSSPs operate Security Operations Centers (SOCs) that monitor your systems around the clock. This continuous vigilance means threats are detected immediately—even at 3 AM on a Sunday when your office is closed and your IT person is off the clock.
Managed Detection and Response (MDR)
Beyond just watching for threats, MSSPs actively respond when something suspicious occurs. They investigate alerts, contain threats, and work with you to recover from security incidents. This combines advanced technology with human expertise to stop attacks before they cause serious damage.
Vulnerability Management
MSSPs continuously scan your systems for security weaknesses, assess the risks, and help you prioritize fixes. They manage the entire process of identifying vulnerabilities, tracking patches, and ensuring your systems stay secure as new threats emerge.
Penetration Testing
Think of this as hiring ethical hackers to attack your systems. MSSPs conduct simulated cyberattacks to find weaknesses before real criminals do, giving you a roadmap for strengthening your defenses.
At ThreatRepel, our comprehensive security assessments go beyond basic pentesting to provide actionable insights that reduce your risk and strengthen your security posture.
Threat Hunting
Rather than waiting for alerts, MSSPs proactively search your environment for hidden threats that may have slipped past initial defenses. This catches sophisticated attackers who try to hide in your systems for weeks or months.
Managed Firewalls and Network Security
MSSPs configure, monitor, and maintain your firewall rules to ensure only legitimate traffic reaches your network. They handle the technical complexity of managing network security so you don’t have to.
Six Key Benefits for Small Businesses
1. Comprehensive Protection Without the Overhead
As your business grows, so does your digital footprint—more employees, more devices, more data, more risk. Building an in-house security program to match this growth requires constant investment in people, tools, and training.
An MSSP provides enterprise-grade protection scaled to your business size. You get comprehensive security coverage without hiring a full security team or investing in expensive security infrastructure.
ThreatRepel specializes in right-sized security solutions for small and medium-sized businesses. We deliver enterprise-grade protection without enterprise-level costs.
2. Instant Access to Security Expertise
Cybersecurity professionals are in extremely high demand and command salaries that most small businesses simply cannot afford. A single experienced security analyst can cost $80,000-$120,000+ annually, and you need multiple specialists to cover different areas—endpoint security, network security, cloud security, compliance, incident response.
Partnering with an MSSP gives you immediate access to an entire team of trained security experts across all these specialties. You essentially rent a portion of a world-class security team at a fraction of what it would cost to build one yourself.
3. Significant Cost Savings
The total cost of cybersecurity goes far beyond salaries. You need:
- Security tools and software licenses ($10,000-$100,000+ annually)
- Security infrastructure and monitoring systems
- Training and certifications for staff
- Incident response capabilities
- Compliance documentation and audit support
MSSPs consolidate these costs into a predictable monthly fee. Many also offer flexible service models where you can choose which security functions to outsource and which to handle internally, optimizing your security investments.
ThreatRepel offers flexible engagement models—from project-based assessments to ongoing security partnerships—ensuring you get the protection you need within your budget.
4. Frees Your IT Team to Focus on Business Goals
If your IT team is constantly firefighting security issues, they have no time for strategic projects that grow your business. Many small business IT teams are already stretched thin managing day-to-day operations—adding security responsibilities on top creates burnout and inefficiency.
By partnering with an MSSP, your IT team can focus on what they do best: supporting employees, maintaining infrastructure, and enabling business operations. The MSSP handles security, creating a powerful collaboration where each team focuses on their core strengths.
5. Access to Advanced Tools and Technology
Cyber threats evolve constantly. Attackers develop new techniques, exploit newly discovered vulnerabilities, and create increasingly sophisticated malware. Keeping pace requires continuous investment in the latest security technology.
MSSPs invest heavily in advanced security tools because it’s their core business. They provide access to enterprise-grade technology that would be prohibitively expensive for a single small business to license and maintain. You benefit from their economies of scale.
Additionally, MSSPs know which tools work best together and how to configure them properly—expertise that takes years to develop.
6. Peace of Mind for Business Leadership
A single cyberattack can devastate a small business. The average cost of a data breach for small businesses ranges from $120,000 to $1.2 million when you account for:
- Lost revenue during downtime
- Customer notification and credit monitoring costs
- Legal fees and potential fines
- Damaged reputation and lost customers
- Recovery and remediation expenses
Beyond the financial impact, the stress of preventing such consequences weighs heavily on business owners and executives. Working with a trusted MSSP alleviates this burden, ensuring your security evolves alongside your business and threats are handled by professionals.
ThreatRepel’s mission is to make businesses cyber-resilient through proactive risk management. We take the burden of cybersecurity off your shoulders so you can focus on growing your business with confidence.
MSP vs MSSP: Understanding the Difference
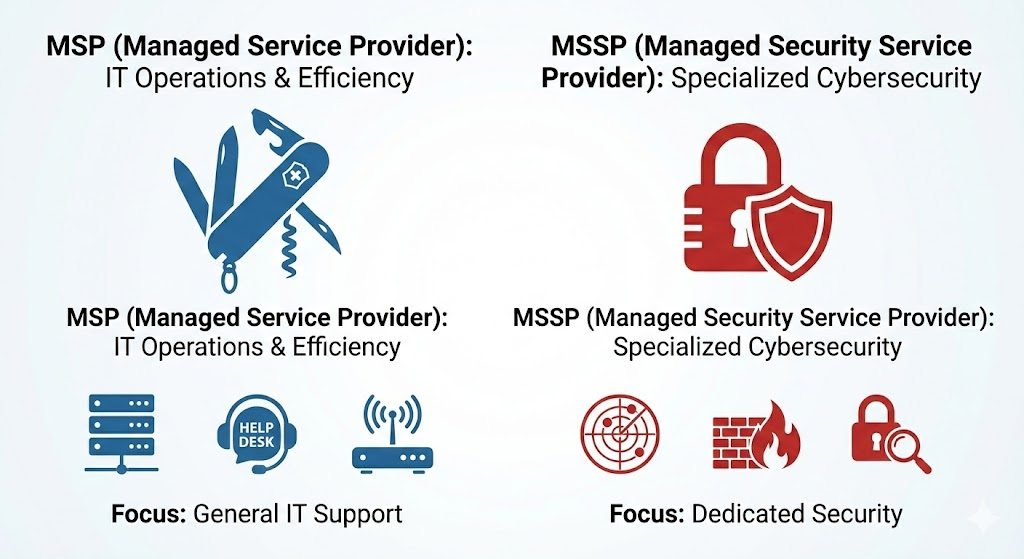
You may already work with a Managed Service Provider (MSP) for IT support. While MSPs and MSSPs sound similar, they serve different purposes:
Managed Service Providers (MSPs) focus on IT operations and business efficiency. They manage your infrastructure, handle help desk support, maintain systems, and ensure your technology runs smoothly for day-to-day business operations. Security may be part of their offering, but it’s not their primary focus.
Managed Security Service Providers (MSSPs) exclusively focus on cybersecurity. They operate dedicated Security Operations Centers, provide 24/7 threat monitoring, and specialize in detecting and responding to security threats.
Many businesses benefit from partnering with both—an MSP for IT operations and an MSSP for specialized security services. Increasingly, established MSPs are also expanding to offer MSSP services, recognizing the growing demand for dedicated security expertise.
ThreatRepel partners with MSPs and IT providers to deliver specialized security services that complement their infrastructure management. If you’re an MSP looking to expand your security offerings, let’s talk.
Is an MSSP Right for Your Small Business?
Consider partnering with an MSSP if:
- You lack dedicated security staff or expertise
- Your IT team is overwhelmed managing both operations and security
- You handle sensitive customer data (payment information, health records, personal information)
- You face regulatory compliance requirements (HIPAA, PCI-DSS, GDPR, NY DFS, state privacy laws)
- You want 24/7 security monitoring but can’t staff it yourself
- You’re concerned about the financial and reputational impact of a data breach
- You need security expertise but can’t afford to hire a full security team
Not sure where you stand? ThreatRepel offers complimentary security consultations to help you understand your current risk posture and whether managed security services make sense for your business.
ThreatRepel’s Approach to Managed Security
At ThreatRepel, we don’t believe in one-size-fits-all security. Our approach is tailored to your business:
Risk-Driven Strategy: We start by understanding your business, your data, and your unique risk profile. Security decisions should be based on actual business risk, not fear tactics.
Transparent Communication: We explain security in business terms, not technical jargon. You’ll always understand what we’re doing and why it matters.
Practical Solutions: We recommend security controls that fit your operational reality and budget. No unnecessary complexity, no shelf-ware.
Measurable Outcomes: We track meaningful security metrics that demonstrate improvement in your security posture over time.
Our Core Services
Comprehensive Security Assessments: Deep-dive evaluations of your security posture with prioritized, actionable recommendations.
Crisis Readiness Assessments: Prepare your organization to respond effectively when (not if) a security incident occurs.
Application Security Program Development: Build security into your software development lifecycle from the ground up.
Compliance Support: Navigate HIPAA, PCI-DSS, NY DFS, SOC 2, and other regulatory requirements with expert guidance.
Managed Security Services: Ongoing monitoring, threat detection, and incident response tailored to your business needs.
Making the Partnership Work
To get the most value from an MSSP partnership:
Be clear about your needs: Understand what data you need to protect, what regulations you must comply with, and where your biggest security concerns lie.
Choose the right service level: MSSPs offer different tiers of service. A small business may not need the same level as a large enterprise—work with your MSSP to right-size the service to your actual risk and budget.
Maintain communication: Your MSSP needs to understand your business, your systems, and your priorities. Regular communication ensures they can protect what matters most.
View it as a partnership: The most effective MSSP relationships are true partnerships where both parties work together toward the common goal of protecting your business.
Real-World Impact: What Our Clients Say
“Working with ThreatRepel gave us the security expertise we desperately needed without the cost of hiring a full-time security team. They helped us achieve compliance and sleep better at night knowing professionals are watching our systems.”
— Technology Company, Long Island
“ThreatRepel’s crisis readiness assessment revealed gaps in our incident response plan we never would have found on our own. When we did face a security incident months later, we were prepared and contained it quickly because of their guidance.”
— Healthcare Provider, New York
Take the Next Step Toward Cyber Resilience
For small and medium-sized businesses, cybersecurity is no longer optional—it’s a fundamental business requirement. Yet building comprehensive in-house security capabilities remains out of reach for most SMBs.
Managed Security Service Providers bridge this gap, delivering enterprise-grade security expertise, technology, and protection at a cost small businesses can afford. By partnering with an MSSP, you gain peace of mind knowing security professionals are watching over your business 24/7, allowing you to focus on growth and innovation rather than constant worry about the next cyberattack.
The question isn’t whether you can afford to work with an MSSP—it’s whether you can afford not to.
Ready to strengthen your security posture?
Schedule a complimentary security consultation with ThreatRepel:
- Visit: threatrepel.com/contact
- Email: assessments@threatrepel.com
- Call: 347-842-9136
Let’s discuss your security challenges and explore how ThreatRepel can help protect your business, ensure compliance, and build cyber resilience—without breaking the bank.
Your business deserves security that works as hard as you do. Let ThreatRepel be your trusted security partner.